Heartwarming Info About How To Control Phishing

While in the suspicious message, select report message from the ribbon, and then select.
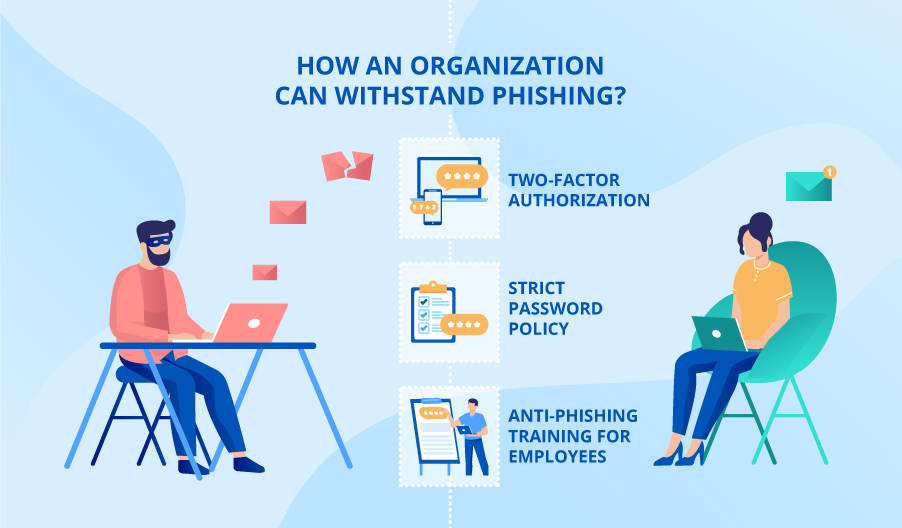
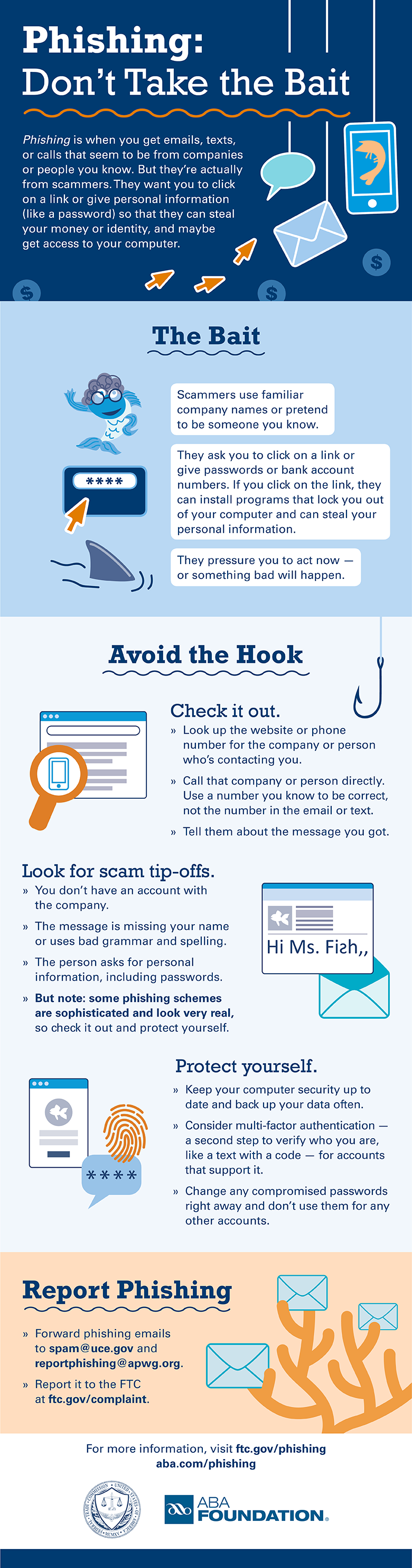
How to control phishing. Use security antivirus and other appropriate security software on. If you have disclosed sensitive information in a phishing attack, you should also contact one of the three major credit bureaus and discuss whether you need to place a fraud alert on your. Fortunately, defending against well researched and expertly written phishing emails is not difficult.
While most do a decent job at blocking spam and phishing attempts, there may still be a few that slip through the. Select the arrow next to junk, and then select phishing. Don’t click on suspicious links if everyone were careful about the links they clicked on, phishing would.
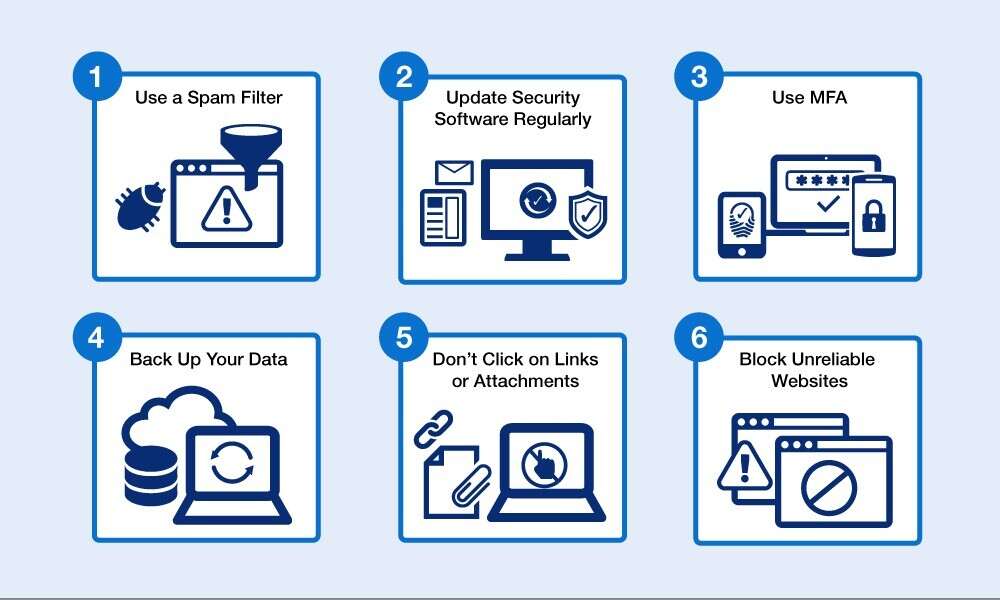
If a recipient's account was compromised. Block consent phishing emails with microsoft defender for office 365 by protecting against phishing campaigns where an attacker is impersonating a known user in the. It’s important to use strong firewalls and updated security filters to block access to any dangerous or illegitimate sites (the same goes for downloads, etc.).
Starting at one of the outermost security layers, prevention of successful phishing attacks begins with strong email security. Deal with any compromised accounts and make sure you block any more phishing messages from getting through. Beyond spam filters, there are steps that users should take to avoid becoming a victim of a phishing attack.
Most software solutions that deal with malware and. Below, we discuss five effective techniques to keep phishing attacks at bay.

.jpg)